People and process
Boundary requires thoughtful considerations around people and processes to maximize its value. It is also necessary to rethink how to position and offer an important platform technology such as Boundary. Changing culture and processes can be difficult, as can organizational and political challenges. Our observations across the industry give us a glimpse into what "good" looks like, which we share below. Please keep in mind that no two organizations are the same, and your specific circumstances may require you to choose how you organize your teams.
Internal developer platform
The Internal developer platform (IDP) has emerged to address the challenge of reducing development cycles and organizational complexity, given cloud computing and IaC have drastically cut down infrastructure provisioning times.
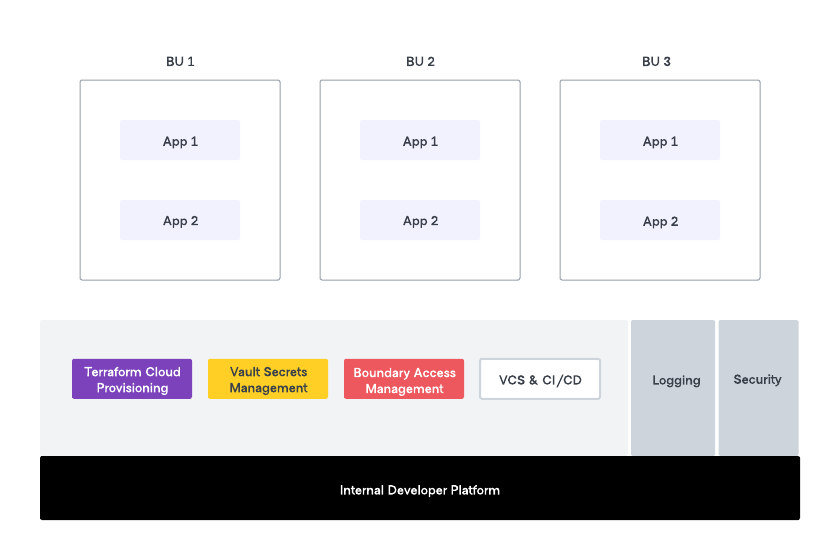
The IDP builds on the time-tested shared service model, improved by adding a product management approach. In this model, a Platform team works with developers to build golden paths that development teams can consume in a self-service model.
Access to infrastructure for developers and other stakeholders is a critical component and hence an Access Management service is an integral part of any IDP. We recommend that the team with ownership of the IDP (the Platform Team) also take ownership of operating Boundary, with the Security Team and other related teams providing governance.
With this approach, there are two key roles: producers and consumers. The terms Producer and Consumer define the roles and responsibilities within a shared service or IDP provided by a Platform team.
Producers
In a shared service model, the producers have a role in configuring the system to meet the needs of the different consumers. Their responsibilities include the following.
- Operating Boundary and ensuring it is available as a mission-critical service.
- Ensuring workflows are well-defined for application teams.
- Set up integration between Boundary and Vault Enterprise for dynamic credentials.
- Work with cross-functional teams to identify targets/hosts to Boundary.
- Enabling consumers.
Producers ensure that the shared services are readily accessible and efficiently utilized by the consumers, empowering them to leverage the benefits of the Boundary platform effectively.
Consumers
In a shared service model, consumers refer to any team within the organization that utilizes the shared services provided by the Platform team. These teams have responsibilities that include:
- Initiating requests for access to targets in Boundary.
- Perform tasks on target systems accessed via Boundary.
Consumers play a crucial role in leveraging the shared services to meet their specific needs and requirements while adhering to the guidelines and standards set by the Platform team.
Platform teams
Platform teams are responsible for overseeing the overall implementation and management of shared tools and services to enable golden workflows, and driving their adoption within the organization. When a platform team matures, they tend towards providing their consumers with a user experience, using the IDP, which integrates with implemented golden workflows.
In the context of Boundary adoption, the platform team ensures efficiency and standardization by establishing and enforcing standards and best practices, promoting consistency across project teams and minimizing the risk of errors and inconsistencies that can disrupt operations. They enable scaling and reusability by enabling automated golden workflows for common user workflows that streamline operations and reduce redundant efforts. These golden workflows include and are not limited to the setting up of Boundary organizations, projects, hosts and host sets (including dynamic host catalogs), credential libraries, credential stores and integrating them with Vault Enterprise for dynamic credentials.
By providing valuable Boundary knowledge and expertise to the consumer community, they serve as a centralized resource for expert guidance. This reduces the learning curve for project teams and ensures consistent application of knowledge throughout the organization.
Platform teams facilitate automation and integration, automating common tasks using IaC and integrating it with other DevOps tools. This streamlines processes, increases speed, and reduces manual errors. They also address the security aspect by ensuring adherence to security best practices in infrastructure setup and maintenance, reducing vulnerabilities to cyber threats.
Platform teams also reduce the time to market for new features and applications. With a mature IaC/Terraform service, they expedite the deployment of new infrastructure, management of the various components of Boundary, enabling faster time to market.
Automation tooling teams
Automation tooling teams are a tactical component of the Platform Team. They manage and maintain the automation and tools required for systems and services to operate effectively. They enable and implement golden workflows for consumers allowing them to use the shared services and tools that are part of the platform effectively. As this team matures, they become the product owners and implementers of the IDP.
Automation tooling teams may comprise multiple teams, each responsible for a different tool or group of tools. The CCoE provides overall strategic guidance for this team, and they collaborate with the consumer community to ensure that the services or workflows they enable meet their needs.
In simpler terms, automation tooling teams are responsible for making sure that the tools and automation used by the Platform Team are working properly. They also work with the consumer community to make sure that the services and workflows meet their needs.
Golden workflows
A golden workflow is a standardized, repeatable process for completing a specific task or achieving a specific outcome. It is typically well-documented and tested, and designed to be efficient and effective. Golden workflows are often used in software development, IT operations, and other business processes.
There are many benefits to using golden workflows. They can help with the below.
- Improve efficiency and productivity
- Reduce errors and mistakes
- Ensure consistency and quality
- Improve communication and collaboration
- Accelerate on-boarding and training
- Facilitate automation
With Boundary, the Platform Team enables golden workflows for federating identity and enabling secure access to remote target systems. The Platform Team empowers application development and other teams to independently access target systems and perform their tasks bound with a session time-to-live (TTL) and dynamic ephemeral credentials while maintaining centralized management and control. The Platform Team oversees and governs these workflows, ensuring compliance with policies, security requirements, and best practices.
Consumer workflows
The Platform Team enables consumer workflows and provide these to the various application development teams.
- Developer workflow: In this workflow the developer can access remote target systems and perform their operations.
- Target on-boarding workflow: This foundational workflow involves on-boarding a target to Boundary. This involves attaching credential libraries and credential stores to a target, setting up automated target discovery workflows if applicable and setting up RBAC policies. Teams use this workflow to onboard newer hosts for secure remote access.
- Credentials on-boarding workflow: For dynamic credentials, this involves determining the secrets storage location within HashiCorp Vault Enterprise for a particular credential and ensuring the credential library can consume those secrets. Security teams use this workflow for the governance of HashiCorp Vault Enterprise to setup dynamic credentials.