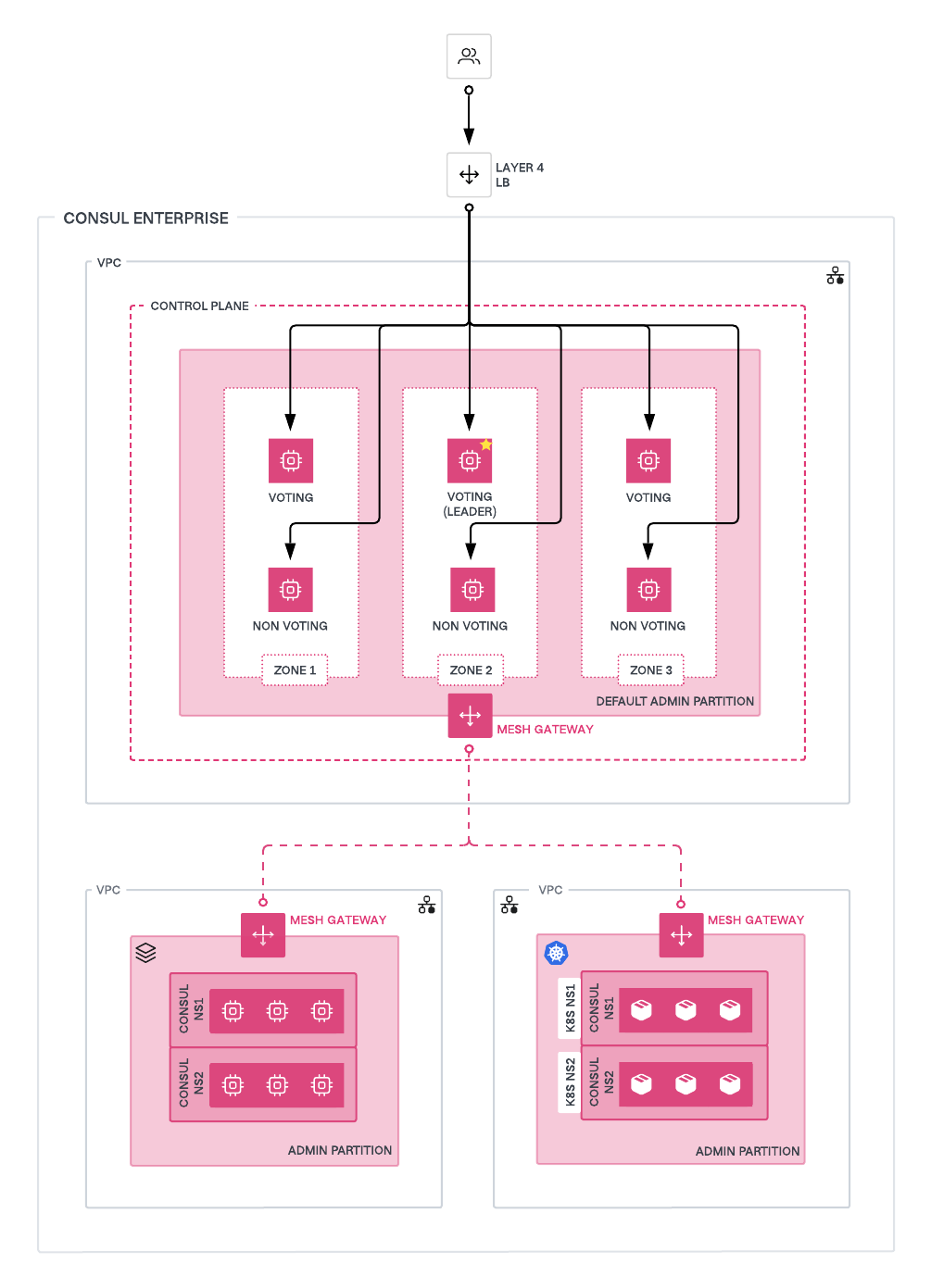
Recommended deployment architecture
We recommend deploying the control plane with 6 server nodes in the Consul cluster, evenly distributed across three availability zones. Configure Consul Autopilot to enable the redundancy zones feature, mapping each availability zone to a Consul redundancy zone. Autopilot will maintain 1 voting server per zone, while the remaining server in each zone will act as a non-voting server. These non-voting servers improve read scalability and can be promoted to voting servers in the event of a voting server failure.
Consul agent configuration
You can create one or more configuration files to configure the Consul agent. The configuration files are formatted as HCL or JSON. The solution design guide recommends HCL and will deploy server configuration in HCL.
The below configuration is required to start the Consul agents in server (server.hcl) and client (client.hcl) mode respectively.
Consul server example configuration
The following is an example Consul server agent configuration.
server.hcl
data_dir = "/opt/consul"
log_level = "${consul_log_level}"
datacenter = "${consul_datacenter}"
encrypt = "${gossip_encryption_key}"
encrypt_verify_incoming = true
encrypt_verify_outgoing = true
server = true
license_path = "${consul_license_path}"
# Configure Redundancy Zones
autopilot {
redundancy_zone_tag = "zone"
}
node_meta {
zone = "${consul_server_availability_zone}"
}
# Enable ACLs
acl {
enabled = true
default_policy = "deny"
}
client_addr = "0.0.0.0"
ports = {
"grpc" = -1
"grpc_tls" = 8503
"http" = -1
"https" = 8501
}
enable_central_service_config = true
advertise_addr = "$INTERNAL_IP_ADDRESS"
retry_join = ["provider=aws tag_key=Environment-Name tag_value=primary-consul"]
# TLS config
tls {
defaults {
verify_incoming = false
verify_outgoing = true
ca_file = "/etc/consul.d/tls/consul-ca.pem"
ca_path = "/etc/consul.d/tls"
cert_file = "/etc/consul.d/tls/consul-cert.pem"
key_file = "/etc/consul.d/tls/consul-key.pem"
}
# overrides tls.defaults path, if specified.
https {
verify_incoming = true
verify_outgoing = true
}
grpc {
verify_incoming = false
}
internal_rpc {
verify_server_hostname = true
}
}
auto_encrypt {
allow_tls = true
}
telemetry {
prometheus_retention_time = "480h",
disable_hostname = true
metrics_path = "/v1/agent/metrics"
}
performance {
raft_multiplier = 1
}
# Server performance config
limits {
rpc_max_conns_per_client = 100
http_max_conns_per_client = 200
}
ui_config {
enabled = true
}
Consul client example configuration
The following is an example Consul client agent configuration.
client.hcl
data_dir = "/opt/consul"
node_name = "consul-client-`hostname`"
log_level = "${consul_log_level}"
datacenter = "${consul_datacenter}"
encrypt = "${gossip_encryption_key}"
server = false
client_addr = "0.0.0.0"
partition = "${admin_partition}"
ports = {
"grpc" = -1
"grpc_tls" = 8503
"http" = -1
"https" = 8501
}
advertise_addr = "$INTERNAL_IP_ADDRESS"
retry_join = ["provider=aws tag_key=Environment-Name tag_value=primary-consul"]
# TLS config
tls {
defaults {
verify_incoming = false
verify_outgoing = true
ca_file = "/etc/consul.d/tls/consul-ca.pem"
ca_path = "/etc/consul.d/tls"
cert_file = "/etc/consul.d/tls/consul-cert.pem"
key_file = "/etc/consul.d/tls/consul-key.pem"
}
# overrides tls.defaults path, if specified.
https {
verify_incoming = true
verify_outgoing = true
}
grpc {
verify_incoming = false
}
internal_rpc {
verify_server_hostname = true
}
}
auto_encrypt {
allow_tls = true
}
#Telemetry
telemetry {
prometheus_retention_time = "480h",
disable_hostname = true
}